Android users beware, the latest vulnerability found in Android-powered smartphones could help cybercriminals to contaminate legitimate Android Apps to launch cyber-attacks. The vulnerability would also let the hackers track infected users without their knowledge. Researchers of Promon Security have found that the vulnerability is capable of infecting most of the Android versions including the latest version Android 10.
Called Strandhogg, the vulnerability could let the hackers retrieve sensitive user data including messages, emails, images, videos and login details saved in the compromised devices. Further, Strandhogg could also allow the hackers to intercept the GPS to track the victim, make or record phone calls and even compromise the smartphone camera and microphone.
Strandhogg vulnerability
Researchers at Promon noticed this vulnerability while investigating a case of illegitimate money transfer from some individual Czech-based bank accounts. Upon analysis, they found the Strandhogg weakness is letting the hackers contaminate legitimate Android apps in the victims' devices to reign over their devices.
The cybersecurity analysts found that myriad of apps have already been infected and are being used to target customers of over 60 financial companies. Till now, Promon has found a total of 36 popular apps getting exploited by the Strandhogg, and over 500 most popular apps in the Android App Store, which are vulnerable to it. Promon researchers have claimed that most of these 36 apps are functioning like the infamous BankingBot, found in 2017.
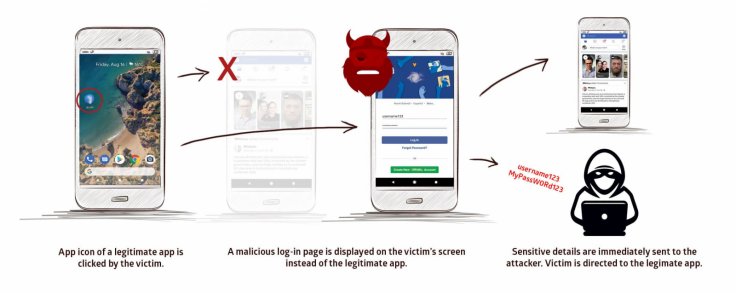
Tricking the device from within
"By exploiting this vulnerability, a malicious app installed on the device can attack the device and trick it so that when the app icon of a legitimate app is clicked, a malicious version is instead displayed on the user's screen," claimed Promon. "When the victim inputs their login credentials within this interface, sensitive details are immediately sent to the attacker, who can then login to, and control, security-sensitive apps," said the cybersecurity firm.
Promon has already reported the vulnerability to Google. While the Android developers can fix the contaminated apps, the Strandhogg vulnerability hasn't been fixed at the time of filing this report.
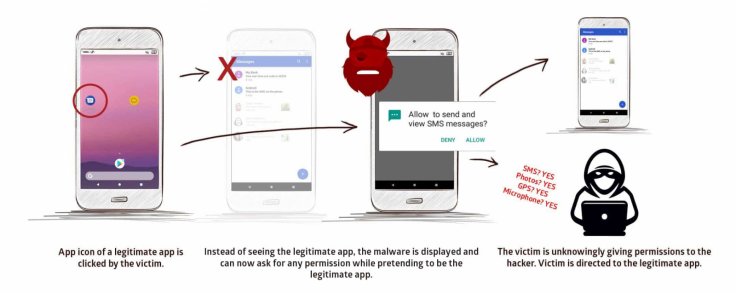
How Strandhogg gets all permissions?
The Strandhogg vulnerability exists inside the Android-powered devices. The vulnerability exploits the multitasking process of the operating system. The multitasking system of Android control settings grants accesses to applications, including malicious ones to run in the system.
Utilizing this vulnerability, an attacker can craft a malicious application to get executed in the system without any interception. While installing these apps, the user might grant all the permission the malicious app asks for. And since it has all the required permits, the app can do whatever they want without informing the users.
However, Strandhogg-infected apps don't exist in the Android official App Store Google Play. It, instead, utilizes the official app as a dropper to download the malware.