
The coronavirus pandemic has rampaged all over the globe, infecting over 2 million people. In an effort to slow down the spread, world governments have already put a third of the global population on an unprecedented lockdown.
In response, businesses have been aggressively shifting their business processes online in order to enable staff to work from home and to continue doing business with customers through digital channels. Cloud-based platforms and software-as-a-service (SaaS) applications have seen an increase in adoption over the past months. But as companies increase their digital transformation efforts, so do their cybersecurity risks.
New scams and hacks have emerged in recent weeks. Google revealed that it has blocked 18 million malware and phishing messages daily related to the coronavirus outbreak on its Gmail platform.
Cybersecurity firm odix, which provides enterprise-grade malware disarm tools, has been among the solution providers looking to help organizations keep their infrastructures safe from threats at such a crucial time.
"It's quite shameful that, even during a pandemic, malicious actors are still trying to victimize companies and users through cyberattacks," odix CEO Dr Oren Eytan shares.

"Because of this, it's important for organizations to not let their guard down. We in the cybersecurity community must be part of the digital frontlines and work to keep organizations safe and secure from new and emerging threats."
Cyber threats during the pandemic
Hackers typically exploit crises to increase their attack success rates, and the coronavirus pandemic is no exception. Hackers take advantage of people searching for information concerning the outbreak by creating dummy websites that seemingly contain relevant information only for them to install malware on their visitors' computers. The malware can steal sensitive information and even cryptocurrencies from infected computers.
With companies now implementing wide scale work-from-home programs, hackers can target online components in order to gain access to these organizations' infrastructure. Weakly protected email servers, online file repositories, and web applications can be particularly vulnerable to breaches and can be used to spread malware across the network.
In addition, staff members may be using their own computers when working from home. These devices often lack the standard protection that most enterprise workstations have, making these companies more vulnerable to threats.
Recently, a new "coronavirus" malware has been reported to be spotted in the wild. The malware is spread through phishing messages that use the promise of financial relief during the outbreak to lure users into downloading or installing it. Depending on the malware variant, it can delete an infected Windows computer's master boot record to render the computer unusable until repaired or wipe the system entirely.
"Central to many of these cyberattacks is the use of malware. Hackers often need some form of malicious program or application to achieve their goals, whether it's to gain remote access to systems or steal sensitive data. This is why we have focused specifically in malware disarm to make sure that none of these malware stay long enough within a network for them to cause any damage," Eytan adds.
Malware disarm at work
odix provides specialized enterprise-grade malware disarm tools that companies can use to deal with malware threats. odix's solution uses content disarm and reconstruction (CDR) as an approach to getting rid of malware.
Hackers typically disguise their malware as legitimate files, with some variants even injecting themselves into actual work documents. More advanced polymorphic malware are even designed to morph or change in order to avoid signature-based detection used by conventional antivirus and antimalware solutions.
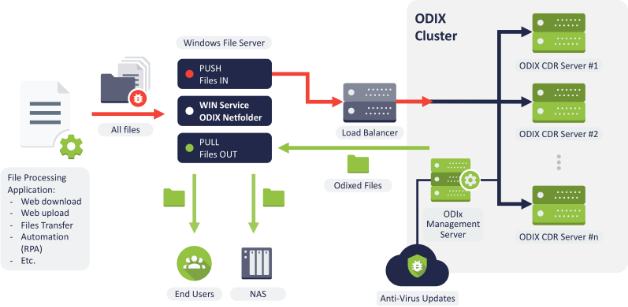
By scanning files at a binary level, CDR can effectively screen for any traces of malicious code. odix also features TrueCDR which keeps the file's type during the sanitization process in order to maintain its usability even after cleanup. This is particularly helpful to organizations looking to mitigate the potential damage malware can have on their work files or intellectual property.
A key advantage of CDR has over conventional approaches is that it can deal with new and emerging malware. Most solutions would first need to have a particular malware to be previously identified and added to their definitions database before the tools would be able to detect and remove them. Even those that use polymorphic code can be effectively screen through odix's deep scanning.
Companies can deploy odix on various components of their infrastructure. It can be integrated with network files applications so that it can scan files in transit. It can be integrated with email servers, allowing odix to scan and sanitize all file attachments even before they reach a staff member's inbox. In addition, odix provides an API that allows developers to enable CDN capabilities in their various enterprise applications. Industrial facilities can also take advantage of odix's Kiosk solution, a dedicated machine that can be used to sanitize files stored in removable storage devices and portable media that are often used with air-gapped control systems.
Resilience during a crucial time
The pandemic has only made the business landscape even tougher for companies to thrive. Achieving business continuity in a pandemic already poses great challenges given all the restrictions to people's mobility. It is unfortunate that cyberattacks have only grown more rampant during this crisis, adding to the hurdles that businesses must overcome.
Fortunately, security solutions are available to provide companies with the means to bolster their security. Advanced solutions like odix can help mitigate the risks brought about by new threats.
"Going through a cyberattack can be devastating to any business during this period. So, building resistance and resilience is crucial to a company's survival. Dealing with cyberattacks is like dealing with disease. Prevention is always better than cure. Putting in place the right tools can prevent attackers from doing any damage to an organization's infrastructure," Eytan concludes.









