In July, it came to light that a Chinese hackers' group was targeting the Vatican and while it briefly stopped the cyberattacks, it is back again despite the previous public disclosure. The group, known as, RedDelta has resumed its operations to break into mail servers of the Vatican and Hong Kong Catholic Diocese.
RedDelta, with alleged links to the Chinese government, has had targeted religious groups to gather intelligence. But the Catholic community has been of particular interest following the pro-democracy protests in Hong Kong. The Vatican had suspended diplomatic ties with China in 1951 after the latter accused the former of espionage. China executed a businessman with ties to the church accusing him of plotting to kill the then Premier Mao Zedong.

Prior Insight
While of late the relations have improved between the two, China has silently been monitoring the churches' activity in the region, especially in Hong Kong. The Vatican was targeted for another reason. China and the Vatican signed a historic agreement earlier this month allowing the Catholic Church to resume operations in the Asian country. But prior to that, Beijing wanted to have insight on the Vatican and thus the hackers' group tried to break into the mail servers, as per security researchers.
Once China's Foreign Minister Wang Yi announced the successful agreement, RedDelta's activity stopped for a while (10 days). But in recent times, they have resumed operations with spearphishing attacks on the Catholic Church.
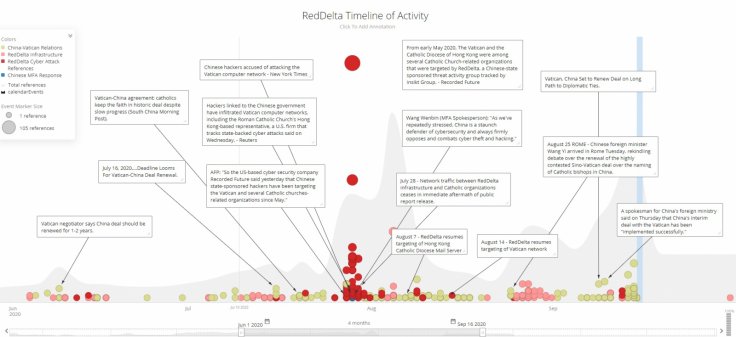
"This is indicative of RedDelta's persistence in maintaining access to these environments for gathering intelligence, in addition to the group's aforementioned high-risk tolerance," researchers at the Recorded Future wrote in a blog post, adding that the resumption of attacks "highlight the Chinese Communist Party's (CCP) focus on gaining increased oversight of the Catholic community within China."
PlugX Trojan
The hackers, known to be associated with Mustang Panda a China-based group of hackers, used RedDelta PlugX, a variety of remote access trojan (RAT) that allows the hacker control over the victim's system without permission or authorization. The PlugX is distributed through email attachments containing a document file that targets mainly Adobe Acrobat Reader or Microsoft Word.
To target the Vatican users, the hackers used documents related to Catholicism in China, Tibet-Ladakh relations and the United Nations General Assembly Security Council to lure victims into opening the files which were preloaded with a .DLL (Dynamic-link library) and a binary file containing malicious code. Once opened, it would give access to the system.



As per the security researchers, RedDelta has used similar PlugX trojan to target non-governmental organizations in East, South and Southeast Asian regions including Myanmar and Mongolia. Recently, Chinese hackers have also targeted law enforcement and government agencies in India following the deadly border clash at Ladakh's Galwan valley.









