A Chinese hacker group swindled over millions from Facebook users with sophisticated malware attacks. Facebook's security team revealed that the gang used a combination of techniques to compromise user accounts and posted fake ads on behalf of them to sell phony products. Despite the short run — between late 2018 and February 2019 — before Facebook's security team caught them in the act, the group made over $4 million.
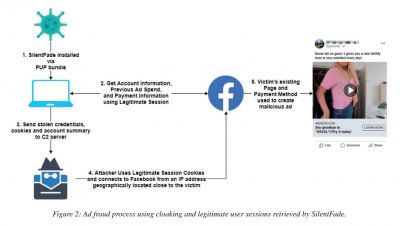
The group targeted users with Windows malware, named SilentFade, malicious scripts and browser injections to overtake users' Facebook accounts. Through the planted malware, they stole Facebook usernames and passwords and checked for the attached payment methods. If they could find any, SilentFade would then place Facebook ads with the user's account.

Ads to Sell Fake Products
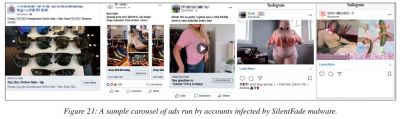
The ads were targeted at specific locations and hence users with whose accounts the ads were purchased wouldn't notice them. The ads were used to sell fake products such as weight-loss products, diet pills, sexual health, handbags, shoes among many others.
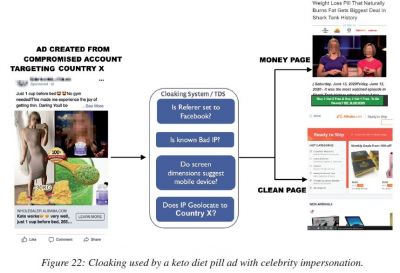
The ads also featured images of celebrities to lure people into clicking them. The hackers used cloaking to mask the destination URLs. "Through cloaking, the defendants deliberately disguised the true destination of the link in the ad by displaying one version of an ad's landing page to Facebook's systems and a different version to Facebook users," the social media giant said. Facebook's security researchers Sanchit Karve and Jennifer Urgilez revealed the details about the malware campaign at the Virus Bulletin 2020 security conference on Friday.
How Did the Malware Spread?
The SilentFade malware was mainly distributed with pirated software. When a user installed the program, it would also infect the system with the malware which would then check for cookies in web browsers. Some cookies contain session tokens with users' login details and even two-factor authentications. If hackers could find such tokens, they could easily gain access to users' Facebook accounts. However, if they could not find any, then SilentFade could collect Facebook login details to hijack the account, Wired reported.
Once the account was hijacked, the hackers used a similar location as the user to make Facebook into believing that it was the user who logged in. They also turned off Facebook notifications for the users so that they would not get any information about another login session. In this case, the hackers also exploited a Facebook bug that made it impossible for users to turn on login alerts and notifications for Facebook Business pages. The social media giant fixed the bug immediately once noticed and also refunded all of SilentFade's victims, whose accounts were charged to place the fake ads.

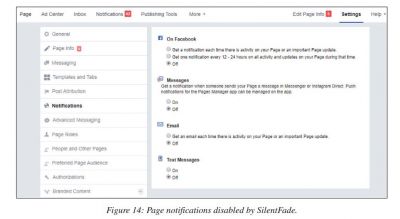
Chinese Connection
Facebook's security team first noticed the ads in late 2018 and following thorough investigation, they found ILikeAd Media International Company Ltd and two Chinese nationals Chen Xiao Cong and Huang Tao responsible for the malware. Facebook sued the company and the two Chinese nationals of ad fraud in December 2019.
However, Karve and Urgilez believe that SilentFade came from another malware named SuperCPA in 2016. The same Chinese group developed the malware to target users within mainland China. "Not a lot is known about this malware as it is primarily driven by downloaded configuration files, but we believe it was used for click fraud – thus CPA, in this case, refers to Cost Per Action – through a victim install-base in China," Karve and Urgilez said in the report.
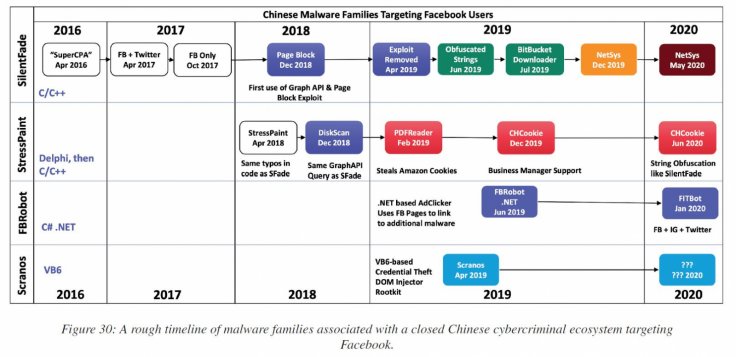
After SuperCPA, it evolved into Stresspaint that cybersecurity research firm Radware found in 2018. In their research, Radware talked about a similar malware named Stresspaint which also harvested Facebook login details. The malware was distributed with a drawing app named Relieve Stress Paint.









