Since 2016 the U.S. intelligence agencies have alleged that foreign state-backed hackers had been targeting the U.S. local and state government agencies. Among them, the most talked about is Russia. On various occasions, cybersecurity researchers and the U.S. intelligence agencies have warned about Russian hackers' attempts but now the U.S. national security officials say that they were successful on two occasions, stealing sensitive data.
The U.S. Department of Homeland Security's Cybersecurity and Infrastructure Security Agency (CISA) and the Federal Bureau of Investigation, on Thursday, said that a Russian hacker's group called Energetic Bear was responsible for the stolen data. The group, also known as Dragonfly, TeamSpy and Berserk Bear among various other names, was actively targeting U.S. government networks including state, local, territorial, and tribal (SLTT) agencies in the last couple of months.

Sensitive Information Stolen
While the names of the government agencies from where the data was stolen were not revealed, the hackers were able to get away with sensitive network configuration and passwords, shared operating procedures (SOP), vendors, purchasing information and printing access badges amongst others, the joint alert said.
"The Russian state-sponsored APT actor has targeted dozens of SLTT government and aviation networks, attempted intrusions at several SLTT organizations, successfully compromised network infrastructure, and as of October 1, 2020, exfiltrated data from at least two victim servers," CISA and FBI in a joint statement said.
How Did They Do It?
CISA also revealed the technical details of the hacking attempts. As per the alert, Russian hackers used several methods to gain access that included brute-force attacks, SQL injection techniques and exploited known vulnerabilities of Fortinet, Microsoft Exchange servers and Citrix.

The hackers also exploited the Windows server's Zerologon vulnerability that allowed them one-click access to the network. Using that, hackers could escalate privilege on Active Directory servers. Apart from that, they utilized compromised Microsoft Office 365 accounts.
In September, CISA said in a statement that the Zerologon might have been used by hackers in the wild. It also urged government agencies to immediately patch the networks. However, it appears that not every department took CISA's warning seriously.
Also, in September, the agency revealed that one of the federal agencies was breached using a sophisticated custom malware (inetinfo.exe) to exploit Pulse Secure VPN's vulnerability. The hacker managed to copy files to a locally mounted hard drive but the agency could not confirm if the data was exfiltrated. But it's possible that the hacker was able to get away with the data.
However, the FBI and CISA said that there was no evidence that the hacked data was used to disrupt services in the U.S. but they warned that the data might be used in future attacks.

"To date, the FBI and CISA have no information to indicate this APT actor has intentionally disrupted any aviation, education, elections, or government operations. However, the actor may be seeking access to obtain future disruption options, to influence the U.S. policies and actions, or to delegitimize SLTT government entities," the alert said.
Voter Information Stolen
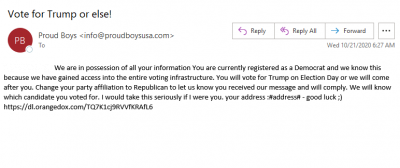
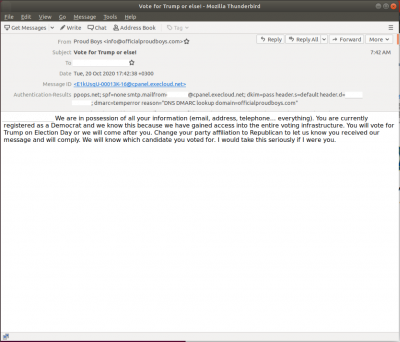
The joint alert came just a day after The U.S. Director of National Intelligence, John Ratcliffe, said in a press conference that hackers from Iran and Russia obtained vital voter information to interfere in the presidential election. It was also disclosed that Iranian hackers posed as 'Proud Boys' and sent spoofed emails to Democrat voters, threatening them to vote for President Donald Trump.
The senders of the emails said that they had access to personal information of the voters by gaining access to the U.S. voting infrastructure. As per ProofPoint, a cybersecurity firm, the emails were sent to voters also contained a fake video showing individual ballot with someone's information. Ratcliffe said the emails were designed to intimidate voters. However, both Iran and Russia have denied the claims.









