For the last few years, the U.S. intelligence agencies have observed a growth in the number of hacking activities from China, allegedly backed by the Chinese government. Their primary target has been U.S. government networks and businesses. The hackers mostly exploit known vulnerabilities to breach into a network to spy, steal data or plant ransomware to extort money.
Recently, the National Security Agency (NSA) had published a list of 25 vulnerabilities that the hackers were actively exploiting. They consider the Chinese hackers "one of the greatest threats" to U.S. National Security Systems, Department of Defense information networks and U.S. Defense Industrial Base. But as per research by cybersecurity firm Check Point, the U.S. isn't the only target. They have been expanding global footprints steadily.

Expanding Global Footprints
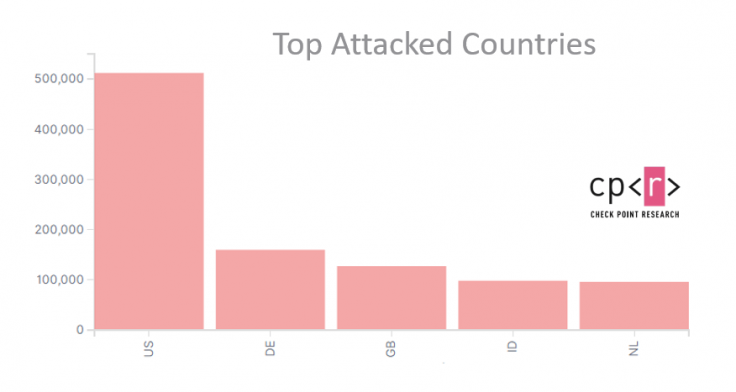
Check Point turned to its real-time threat intelligence platform ThreatCloud to understand the global impact of the vulnerabilities listed by the NSA. They found that while the U.S. was the number one target of the Chinese hackers with over 500,000 attacks, Germany, the United Kingdom, Indonesia and the Netherlands were also faced significant cyberattacks.
"Following the NSA report, we wanted to see what's going on worldwide on attacks targeting those vulnerabilities, as those are on high-profile products, such as Microsoft, Adobe, and the majority of them may have a severe impact," Adi Ikan from Check Point's network research and protection team told DarkReading.
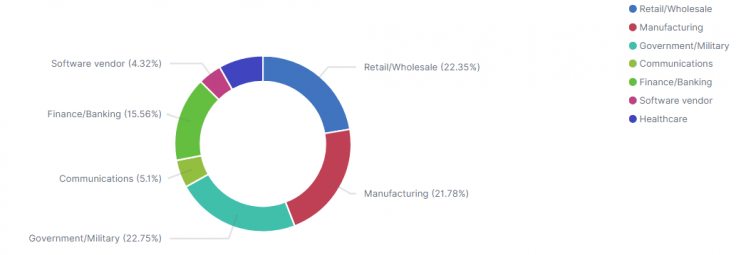
The hackers use a range of tactics to break into networks including phishing, brute-force, malware attack and exploiting vulnerabilities. The primary focus in the U.S., as per the research, seems to be more on government and military networks compared to other countries. Ikan said that even government and militaries from Canada, Spain and Denmark have also been targeted.
Common Exploits
Ikan said out of the listed vulnerabilities, few were easy to exploit. For example, Atlassian Confluence Server's remote code execution vulnerability (CVE-2019-3396) has been exploited often. He also noted that flaws with severe impacts and issues in high-profile tools were often targeted by hackers.
Apart from that, DrayTek Vigor VPN routers' Command Injection vulnerability (CVE-2020-8515) has also been exploited more often. The other mostly exploited security issue is Microsoft Windows NTLM Authentication Bypass (CVE-2019-1040). It allows a man-in-the-middle bypass the NTLM Message Integrity Check (MIC) protection. The other two Check Point listed in its top five vulnerabilities included Pulse Secure VPN's flaw (CVE-2019-11510) and Citrix's CVE-2019-19781 security issue.
The last two vulnerabilities have been widely exploited across the world. Pulse Secure VPN's flaw allows an attacker remote access without any authentication. The hacker can perform an arbitrary file reading to expose passwords. This vulnerability was recently used to target a U.S. government network and the hacker was able to copy data to a mounted hard-drive.
Then there is the flaw in Citrix's Application Delivery Controller and Gateway. It has been widely exploited with the notable one being in a German hospital. As a result of that, a patient died, becoming the first known casualty of a cyberattack. Check Point also noted CVE-2020-5902 being used by the Chinese hackers. This remote code execution vulnerability in F5 BIG-IP proxy devices allows hackers unauthenticated access to the Traffic Management user interface.
For all those vulnerabilities, patches have already been released and intelligence agencies have advised applying the fixes immediately. However, network administrators fail to apply the fixes helping hackers take advantage of the situation.









