Hackers use various methods to target their victims. More often than not hackers exploit an existing vulnerability in the system or lure users through a phishing email. Now, they have come up with another unique way — mimicking McAfee antivirus to trick users into downloading the malware.
According to Google's security team, the new trick has been developed by a Chinese hackers' group APT31, also known as Zirconium, and their primary targets are high-profile people, including the U.S. Democratic nominee Joe Biden's Presidential election campaign. Google said the target was to overtake the personal email accounts of his staff.

In a blog post on Friday, Google's security team revealed that they had identified phishing email links that were designed to lure victims into downloading malware that was developed using Python code. Through that, hackers could alter the malicious code using Dropbox, a free cloud storage service.
"The malware would allow the attacker to upload and download files as well as execute arbitrary commands. Every malicious piece of this attack was hosted on legitimate services, making it harder for defenders to rely on network signals for detection," said Shane Huntley, a security researcher from Google in the blog post.
Disguising as McAfee Antivirus
The most interesting aspect of the hacking attempt was that they developed a sophisticated technique to disguise the phishing attempt in a legitimate version of McAfee antivirus software. "The targets would be prompted to install a legitimate version of McAfee antivirus software from GitHub, while the malware was simultaneously silently installed to the system," Huntley said.
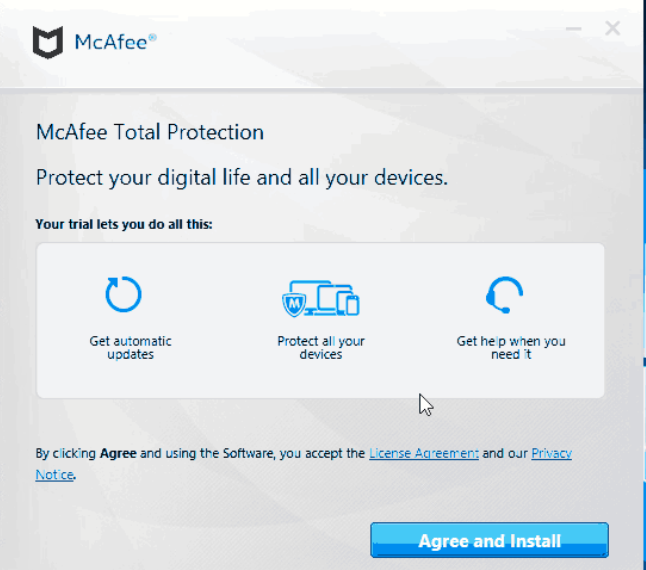
However, the malware attack didn't only target Biden's campaign staff. Previously, Microsoft also noted that prominent members of the international affairs community, academics from over 15 universities were targeted. The use of a popular antivirus software McAfee may come as a surprise but Google says state-backed hackers have previously used legitimate software to disguise malware.
Google said the attacks were from a Chinese hacker's group named APT31 which is allegedly tied to the country's government. The tech giant had developed a warning system and filtered most of the malicious attacks in the past, If Google's system detects a state-backed hacking or phishing attempt, it sends out a warning, explaining that a foreign government might be responsible. Huntley said that Google had already shared the findings with the FBI.
Microsoft in its last month's blog also noted that at least a staff of U.S. President Donald Trump's re-election campaign was also targeted by APT31. Besides the Chinese group, an Iranian hacker group known as APT35 also had been targeting Trump's campaign with phishing emails.









