State-sponsored hacking has been around since ages, with one country snooping on others' diplomatic and military intelligence to gain strategic advantage. To accomplish their mission, they adopt numerous devious ways. In the latest instance, members of the Palestinian militant group, Hamas, have reportedly compromised a few Israeli soldiers' smartphones.
According to a Reuters report, a spokesperson from the Israeli Defense Force (IDF) has claimed Hamas militants had posed as attractive women to compromise the victims' devices. Once they took control of the target devices, Hamas operatives installed malware in them to snoop on the Israeli soldiers. The IDF has claimed that Hamas militants created fake social media profiles on Facebook, Instagram and the messaging app Telegram.
The honeytrap
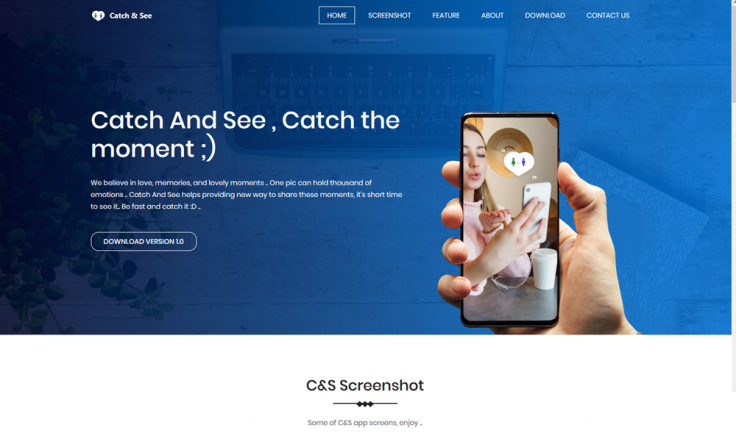
The IDF spokesperson added that the militants camouflaged as Israeli immigrant women with little knowledge of Hebrew. Through an investigation, the IDF got to know about the dummy accounts that used female names such as Sarah Orlova, Maria Jacobova, Eden Ben Ezra, Noa Danon, Yael Azoulay, and Rebecca Abaxis.
Once befriended, the compromised Israeli soldiers were asked to install chat apps dubbed Catch & See, Grixy, and Zatu to get explicit images. According to Gen. Silberman's statement, once they tap on the install icon of the disguised apps, they would prompt a message to notify those apps can't be installed. Once compromised, the app installer icon would auto-destruct itself to stay away from any suspicion and installs malware in the device.
The malware

The malware is capable of running in the background and sending all images, messages, contacts and other user data to a command-and-control server. It could also track the current GPS location, take screenshots and install other malware into the system.
The malware attack process is also capable of bypassing Google Play's protection protocol to stay in the App Store and breach other potential victims.
Earlier instances
This is not the first instance where Israeli soldiers have been compromised. In 2017, soldiers at the Gaza Strip were compromised with spyware called Viperat. The attackers used social engineering techniques to compromise devices' images and audio files. A CheckPoint blog claims that the Pakistani army too used a Russian APT group to install specially-crafted malware called SmeshApp in many devices of Indian army military personnel in 2016.









