Last year major security bugs were disclosed in a large number of enterprise VPN servers. It includes those which were sold by Pulse Secure, Palo Alto Networks, Fortinet and Citrix. The offensive campaign, named as "Fox Kitten Campaign" was revealed by ClearSky research team.
The researchers have published a new report which revealed that Iran's government-backed hacking units have made a top priority in 2019 to exploit VPN bugs after they became public in order to infiltrate and plant backdoors in world companies.
Report on Iranian hackers
The new ClearSky research report revealed that the Iranian hacking group targeted companies all around that word which included IT, Telecommunication, Oil and Gas, Aviation, Government as well as Security sectors. This security report also mentioned that the Iranian hackers are not sophisticated and less talented than other cybercriminals from Russia, China and North Korea. They also noticed that Iranian threat actors were exploiting VPN flaws within hours after the bugs been publicly disclosed.
As per the report, the researcher claimed that "Iranian APT groups have developed good technical offensive capabilities and are able to exploit 1-day vulnerabilities in relatively short periods of time."
Last year, Iranian groups were quick to weaponize vulnerabilities which were disclosed in the Fortinet FortiOS VPN, the Pulse Secure "Connect" VPN and Palo Alto Networks "Global Protect" VPN. The attacks against these systems took place last summer but they have also continued it in 2020.
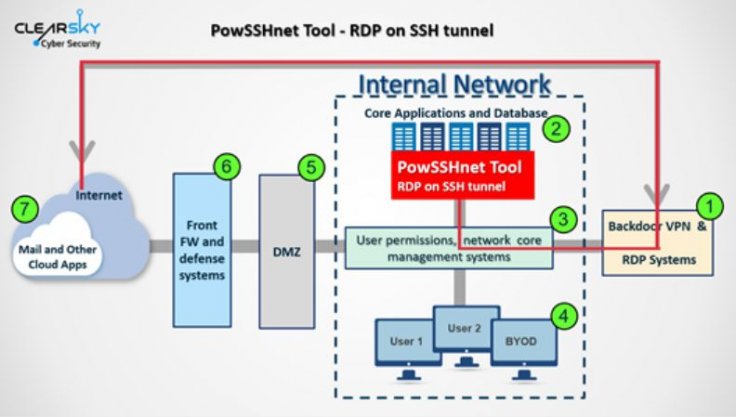
Planting the backdoors
In the report, researchers revealed that the purpose of these attacks is not only to breach enterprise networks but also to move laterally throughout the internal systems and plant backdoors to exploit. While during the stage of network violation, the hackers targeted VPNs, in the second stage they showed the collection of tools and techniques which showed how advanced these Iranian hackers have become in recent years.
These hacking unit also exploited open-sourced hacking tools like JuicyPotato and Invoke the Hash. The report revealed that they also used legitimate sysadmin software like Putty, Serveo, Plink, Ngrok or FRP. These hackers also knew how to develop custom malware to support their attacks in case of the absence of open-source tools or local utilities.
ClearSky found tools like:
As per the report, the cyberattack campaign also included some infrastructure which was used to develop and maintain access routes to the targeted organizations, steal valuable information from the targeted organizations, maintain a long-lasting foothold at the targeted organizations and breach additional companies through supply-chain attacks.