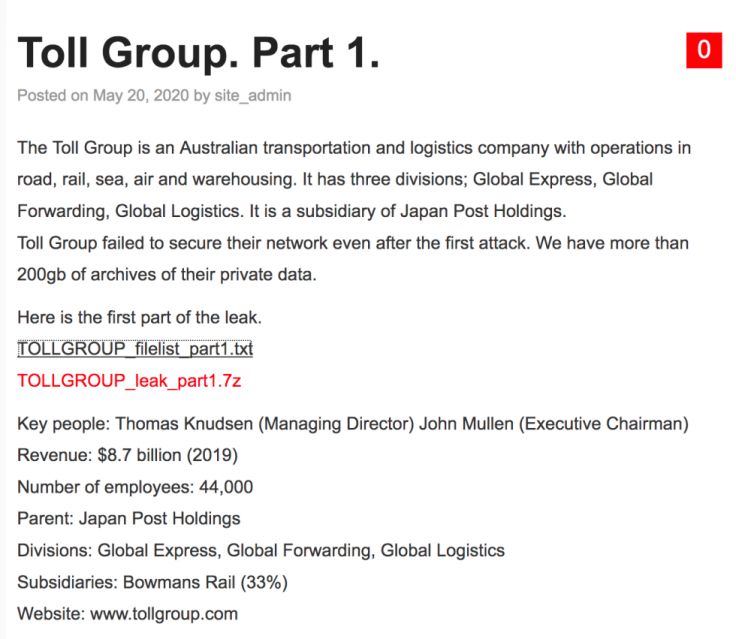
The Netflim ransomware operators have leaked the first installment of data from a massive 200 GB worth data of the global logistics company Toll Group. The operators have hacked the Toll network via its ransomware at the beginning of this month and breached a massive volume of data before encrypting the Toll network. The ransomware operators have leaked the data consolidated in compressed files along with a note.
The leak note mentioned that the leaked data is the first installment from the lot they have compromised. However, the threat actor hasn't mentioned anything regarding the ransom money they asked. The message was posted on the operator's onion site, hinting the initial ransom discussion between the operator and the authorities at Toll Group.
The Earlier attack

Significantly, the Japan Post Holdings subsidiary company has fall prey to ransomware attacks twice in 2020. The Netfilm attack was executed at the beginning of May, while a MailTo ransomware compromised Toll's global network on January 31 this year. In the earlier attack, the ransomware had taken down over 1000 servers, which compromised around 500 corporate applications, Active Directory, and other critical systems. After the MailTo ransomware attack, the global operation of the company was suspended for several weeks. Toll Group officially confirmed to take its network in the second week of March.
But, while fixing the network, the system admins might have overlooked a backdoor, which was later exploited by the Netfilm group of ransomware operators.
In its official system update section, Toll Group said, "Following our announcement last week that a ransomware attacker had stolen data contained on at least one Toll corporate server, our ongoing investigation has established that the attacker has now published to the dark web some of the information that was stolen from that server."
"As a result, we are now focused on assessing and verifying the specific nature of the stolen data that has been published. As this assessment progresses, we will notify any impacted parties as a matter of priority and offer appropriate support," it added.
How Netfilm ransomware works?
The Netfilm ransomware resembles a notorious ransomware Nemty 2.5 and attacks the network mostly via Remote Desktop Services. However, unlike Nemty 2.5, the Netfilm doesn't have a Ransomware-as-a-Service option (RaaS) and depends on email communication instead of Tor sites for collecting money, noted BleepingComputer.
The Netfilm ransomware uses AES-128 encryption methods for encrypting the victim's file with an RSA-2048 public key. The public key gets embedded later in the ransomware executable file. The ransomware also adds a .netfilm extension at the end of each file.









