Ransomware attacks across the globe have seen a sharp spike over the last few months. Many enterprises and even government agencies have fallen victim to the attacks. One of the most trending ransomware has remained Netwalker which has preyed on numerous large enterprises.
The Victims
According to researchers at Cyble Inc, Netwalker has hacked large enterprises such as Inventus Power, Barbizon Capital and the City University. In all the instances, the ransomware operators have released a chunk of highly sensitive data in its own dark web-based site to compel authorities to meet its demand.
The ransom amount is not known yet. Ransomware operators usually fix the amount according to the sensitivity of the stolen data and the volume of the company.
Inventus Power is one of the biggest integrated power system suppliers for global OEMs for the past six decades. O2Micro too is a reputed company and works as an innovative power management component supplier to many computer, consumer, industrial, automotive, and communication companies.
The Netwalker ransom operators had earlier hacked Nicholas Rick & Co and Barbizon Capital.
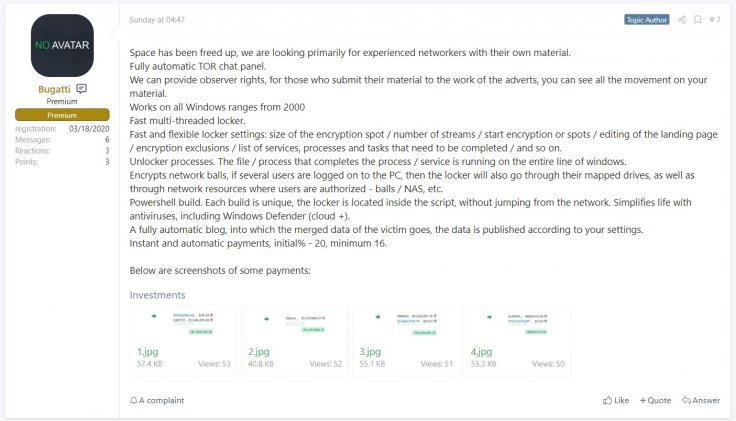
Ransomware Affiliates
The Netwalker alias MailTo has been around for the past few years. Alongside attacking large enterprises, MailTo offers the ransomware as a Software-as-a-Service (SaaS) model and recruits associates with promises of enormous money-making opportunities. For each successful attack, an affiliate receives around 70 per cent of a ransom deal which often goes beyond millions of dollars.
How Netwalker Ransomware Works
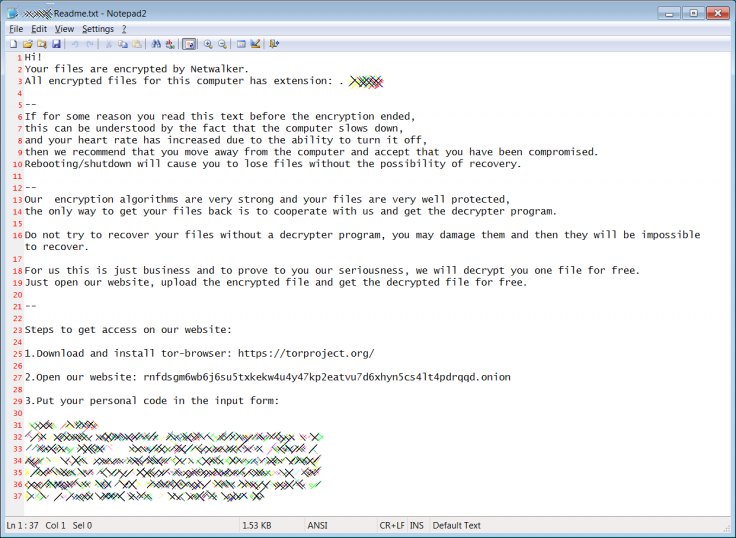
The Netwalker aka MailTo usually spreads via convincing phishing emails such as coronavirus- related health alerts from reputed authorities. The mail goes with a malicious attachment written in VB Script. It is capable of taking over the victim's machine by a just a double click.
Once the ransomware gets executed, it encrypts all the files in the device. It adds a random extension to the encrypted files. Once the encryption process is complete, the ransomware operator sends detailed instructions regarding the ransom money, deadline and payment procedure.