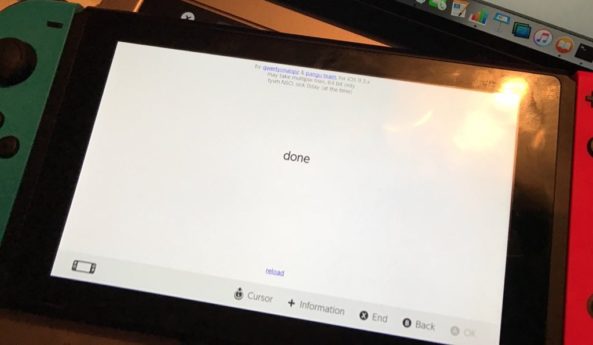
Nintendo's newly released game console, the Switch, is allegedly shipped with an outdated browser whose WebKit version remains vulnerable to browser-based exploit used by iOS hacker Luca Todesco in jailbreaking iOS 9.3.x. The browser vulnerability details for the console have been revealed in the proof-of-concept created by LiveOverflow.
The WebKit exploit aka JailbreakMe uses an arbitrary code in Safari browser to bypass certificate issues and thereby enable Pangu users to re-jailbreak iOS 9.2-9.3.3 indefinitely. Although the exploit seems to be patched up in latest versions of iOS 9.3.5 and higher, the Nintento Switch still carries the critical vulnerability in its bundled browser, which is mostly affected when a hijacked website or portal is accessed via unsecure Wi-Fi networks.
There is no fully working jailbreak tool available yet which is based on the JailbreakMe exploit. However, the exploit itself can be hooked to the Switch by simulating a captive portal on a laptop for launching the integrated browser within its Wi-Fi settings. Consequently, the hijacked site or portal will be redirected to a specific webpage or an adapted JailbreakMe exploit page.
Meanwhile, Nintendo is expected to roll out a bug-fix update to address the exploit without requiring user authentication and thereby prevent its execution or use with a hack tool.
[Source: iDownloadBlog]










